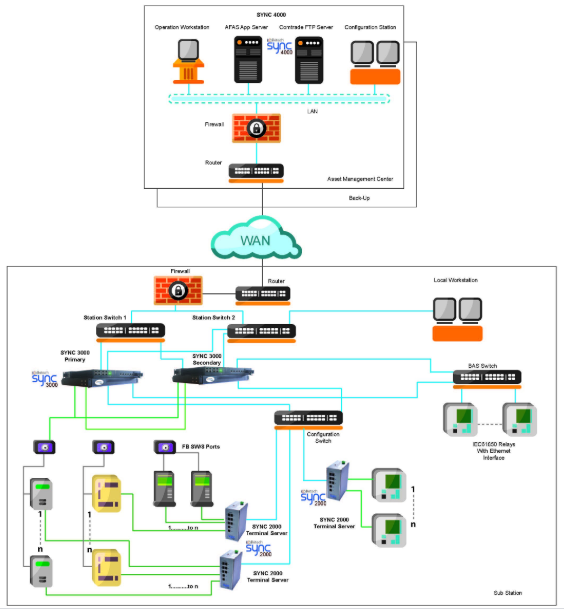
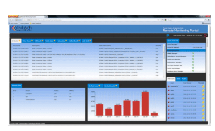
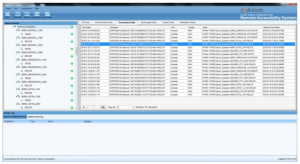
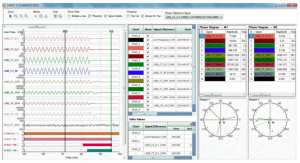
Disturbance Data Handling:
Comparative analysis of disturbance data generated by devices at various locations across the network has been a challenge for protection engineers and system operators. Along with the Kalkitech substation data concentrator, PSES collects disturbance data from various sources including event loggers and protection equipment. This data is made available in a common format for further analysis. PSES also provides a visualization interface for viewing and analyzing disturbance records. Protection operation/substation events from event recorders are also displayed to aid effective analysis of disturbance events. The disturbance data is tagged and archived in a central database and users can initiate analysis of any past fault
User Authentication: PSES includes a mechanism for remote configuration of substation equipment. The system should be configured to ensure access to authorized users only. PSES provides configurable
user roles that can be assigned to individual users. Activities performed by each user is logged by the system, creating an audit trail
Remote Configuration: PSES enables configuration/programming of remote IED from a central location using the vendor-supplied tools. The system automatically archives the configuration into backup files after modification. PSES allows easy retrieval of archived configurations along with an audit trail. These backups are mirrored into redundant storage locations.
Disturbance Viewing: PSES is equipped with an optional module to view waveforms and phasors to analyze the disturbance data retrieved from various devices.
Online Device Monitoring: The runtime view of PSES provides details about the status of each of the configured assets. This includes NMS Information mapped through SNMP, Alarms, and events filtered for a particular device or group of devices and a summary in a web-based dashboard.
Redundancy Support: PSES supports hosting of the control center in multiple locations with redundant servers at each location. The redundancy Manager of PSES synchronizes user files and the database between redundant servers. Failure are automatically detected and the switch over to the redundant system occurs automatically.